Sophos Firewall
- Authentication -
Users and Groups
Summary
Standard Users
username and password, locally or externally
Clientless Users
IP address, locally
Guest Users
system generated username and password, locally
Types of Users
Standard Users:
- Authenticate with their own username and password
- Can be locally or externally authenticated using an external authentication server such as Active Directory
Clientless Users:
- are purely identified by their IP address
- Always authenticated locally by the Sophos Firewall
- example: control network access for servers or devices such as printers and VoIP phones.
Guest users:
- Authenticate with a username and password, generated by the Sophos Firewall
- Always authenticated locally by the Sophos Firewall
Configured in:
CONFIGURE – Authentication – {UserType}
Types of Groups
A group is a collection of users with common policies and can be used to assign access to resources.
The user will automatically inherit all the policies added to the group.
Example policies that can be applied to groups:
- Network Traffic
- Surfing Quota
- Access Time
Configured in:
SYSTEM – Profiles
Types of Groups:
- Normal Groups
- Clientless Groups
Groups are managed in:
CONFIGURE – Authentication – Groups
Import Groups from Active Directory
Using AD, users will be created on the Firewall and assigned to a group when they first successfully login.
To use AD groups you must use the import wizard before users login
Note:
Sophos Firewall groups cannot be nested therefore, if a user is a member of multiple groups, they will be added to the first one they match.
Authentication Methods
Summary
1
Hotspot
2
Clientless Users
3
Single Sign-On
4
Authentication Agent
5
Captive Portal
Authentication order
The order in which authentication is checked for users:
- Hotspot
- Clientless Users
- SSO
- Authentication Agent
- Captive Portal
Single Sign-On (SSO)
–
Synchronized User Identity
Synchronized User Identity will work by default if the following prequisites are satisfied:
you must have
- added an Active Directory authentication server on the Sophos Firewall
- imported the groups using the wizard.
- enabled the Active Directory authentication server as an authentication source for the Firewall in
CONFIGURE – Authentication – Services
All Windows endpoints with a heartbeat to the Sophos Firewall will be authenticated transparently
Disabling Synchronized User Identity
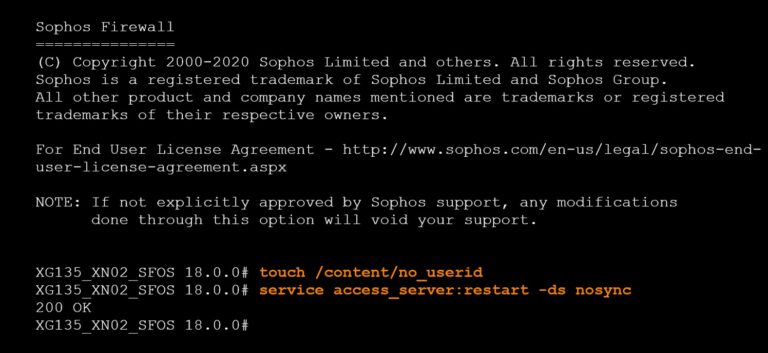
Via the console it’s possible to disable Synchronized User Identity by creating the file /content/no_userid
Removing this file will re-enable Synchronized User Identity again
Note:
You must restart the authentication service to apply this change
Web Authentication
lorem ipsum dolor
Sophos Transparent Authentication Suite (STAS)
STAS provides transparent SSO authentication for users without requiring a client on the endpoint.
How it works:
- Uses an agent installed onto the domain controller
- Requiers one STAS installation serving each domain controller
- Provides SSO without a client on the endpoints
- Supports only IPv4
STAS event log: Port 6060
Event ID = 4768, (on Windows 2003: Event ID = 672)
Configured in:
CONFIGURE – Authentication – STAS
Authentication Agent
Authentication Agent uses an agent on each endpoint.
The agent shares the MAC address, this allows to use MAC address restrictions.
Captive Portal
The captive portal is a browser interface that requires users connected to the firewall to authenticate when attempting to acces a website.
After authenticating the user proceeds to the address or the firewall redirects the user to a specified URL.
https://www.youtube.com/watch?v=q0GwtPLS0nk
Chromebook Single Sign-On
Chromebook SSo must be enabled by providing your domain that is registred with G Suite and certificate used to communicate with the Chromebook
Notes:
- enable the Chromebook SSO service in device access for the zones where the device is located
- create a firewall rule that allows the Chromebook to access the Google API and Chrome Web Store
- upload the Configuration as a JSON file in G Suite
Configured in:
CONFIGURE – Authentication – Services
Using Authentication
Firewall Rules
Enable the option “Match known users” and select the users and groups to match on.
This makes the firewall rule from a “network rule” to a “user rule”
If the firewall rule is used for business applications like Office 365 you can exclude the traffic from data accounting
Web Policies
you can create web policy rules that apply to specific users and groups.
for example: Apply web filtering rules to specific users and groups
Web Server Authentication
Protect access to a web server by forcing users to authenticate before the connection even reaches the destination server.
Attackers cannot try to exploit the web server as they don’t have access to it.
One-Time Passwords
How OTP authentication works
The user has a token that contains a key and gets the time from a synchronized clock
The Sophos Firewall needs to have the same key and be synchronized to the same clock so that when it calculates the token code it comes out with the same number.
RSA tokens are not supported
Enabling OTP
One-time passwords are disabled by default.
It can be enabled for either all users, selected set of users or groups.
Configured in:
CONFIGURE – Authentication – One-time passwords